It’s taken over a decade for us to get here, but the time has finally come for cloud security to take pole position in the CISO priority list. With increased cloud adoption, data accumulation, and the steady passage of time, enterprises have gone through a discovery process to understand which tools are most needed at each stage of their cloud journey. While the last decade has been an obvious growth period for cloud providers like AWS, it’s also created knock-on opportunities for startups that can secure enterprises on the frontier of their migrations. I had the privilege of watching the early innings of this story unfold during my years at Rubrik, and again from the sidelines following the meteoric success of Wiz. Both companies famously scaled to $100m ARR in six quarters, and did so by solving the most pressing cloud infrastructure and security-related challenges of their respective moments. Four years removed from Wiz’s initial breakout success, we’re now seeing the market take yet another turn.
While CSPM has proven to be a brilliant starting point for enterprises building out their cloud security programs, attackers have continued to find their way in, and the market has responded with dozens of exciting new categories. Wiz’s Assaf Rappaport himself has recently stated that “2024 will be the year of acquisitions,” a clear acknowledgement that there is still a world of opportunity here beyond CSPM. Their recent acquisition of Gem Security marks their advancement into the CDR market, and I believe their continued expansion will illustrate that cloud security is a vast problem space with demand for many different types of products.
Rubrik, Wiz, and cloud adoption over time
The main trend driving this market is a foregone conclusion, but is still worth pointing out: companies are going to the cloud. AWS is a big deal, and becoming an even bigger deal.
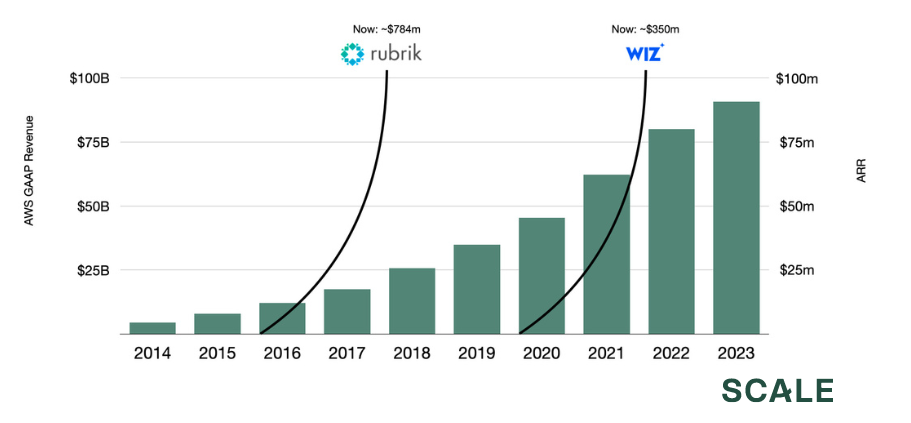
When you place Rubrik and Wiz side-by-side, the timing, sequence, and scale of these two companies tell a nice story about how we got here. Ultimately, the Rubrik story is about a company that helped facilitate one of the largest sea-changes of the last 20 years: the gradual-but-massive shift to the cloud. While the company has done a tremendous amount of work to move into the security market in recent years, they initially started off as an on-prem backup vendor. When Rubrik first started selling in 2016, cloud adoption was primarily for greenfield applications, and enterprises still had massive on-prem infrastructure investments that they were looking to modernize. Private data centers included sensitive production systems, but they also included petabytes of old, stale backup data that needed to be held onto for compliance reasons. For these companies, Rubrik offered a brilliant way to kill two birds with one stone: (1) initiate your cloud migration by moving your lowest-stakes data first (your backups), and (2) simplify and automate your entire backup operation while you’re at it. With this feature alone, the company broke records, scaling to $100m ARR in 6 quarters, largely by capitalizing on the initial urgency for cloud migration.
That was 2017. Fast-forward to 2024, and the company’s S-1 highlights just how far this tailwind has taken them: to $784m in ARR. On a personal note, being along for that ride for four plus years was more fun than I knew you could have in an office environment.
Wiz’s story started in 2020, and was only possible in a world that existed four years after Rubrik. Once enterprises were further along in their cloud adoption and had more production workloads running in the cloud, the immediate opportunity that followed was for surfacing misconfigurations on that infrastructure. They entered the market with a lightweight, agent-less product that could be deployed and begin adding value in minutes. Similar to Rubrik, they met the market where it was, and achieved a similarly astonishing outcome: six quarters to $100 million ARR.
What binds these two companies is that they followed customers along their cloud migrations and delivered services that met the needs of that moment. Rubrik helped companies get off the ground in 2016, and Wiz helped them land correctly in 2020. Four years on from Wiz’s explosive debut, we’re now seeing the next batch of security challenges emerge. Attackers are increasingly targeting threat vectors that a CSPM or understaffed security team wouldn’t be able to prevent, such as the emerging popularity of hijacking Kubernetes clusters or breaching service accounts adjacent to cloud infrastructure. Security leaders (and Wiz themselves) have rightly recognized that while CSPM is a great start, there is still much more to be done. And if there’s anything we can learn from the Rubrik and Wiz success stories, it’s that the reward for solving these emerging challenges can be massive.
New categories and opportunities
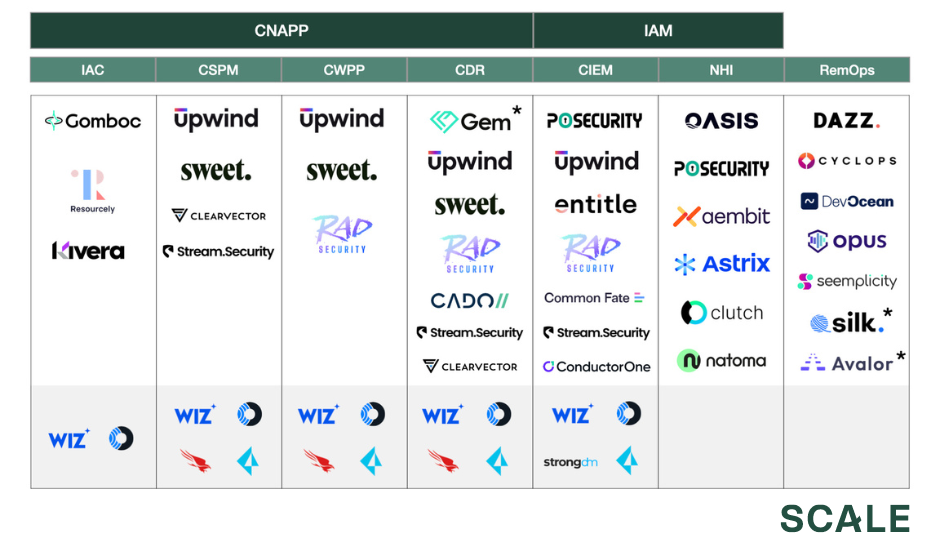
Note: Asterisk denotes acquisition. Gem acquired by Wiz; Avalor acquired by Zscaler; Silk Security acquired by Armis.
The security industry is notorious for its alphabet soup of acronyms, so a few clarifying definitions are in order. Many of these categories are still being fleshed out in real time, and there are certainly some important nuances that separate companies within each bucket. With that said, here are a few high-level overviews:
- Infrastructure as Code (IAC) Generation/Scanning: IAC is a method of defining your infrastructure configurations in code, rather than leveraging your cloud provider’s UI/console. This has gained tremendous popularity over the last decade, as evidenced by the success of companies like HashiCorp and tools like Terraform, AWS CloudFormation, etc. Given that IAC templates are essentially ground zero for infrastructure configurations, the “furthest left” practice in cloud security is scanning, generating, or modifying these templates to prevent misconfigurations in the first place.
- Cloud Security Posture Management (CSPM): This category has been the beachhead of the cloud security market, driving the majority of Wiz’s growth over the last four years. CSPM tools are broadly preventative in nature and focus on surfacing misconfigurations in your infrastructure, such as unrestricted inbound ports creating exposure to the internet, unrestricted outbound ports creating opportunities for data exfiltration, unrotated access keys, unencrypted data stores, and more. These products are typically agent-less, meaning that customers don’t need to deploy additional software in their environment. This is a huge plus, as it means you can deploy the product and experience value in a matter of hours, even at enterprise scale. Buyers can simply grant admin permissions to the CSPM tool, which then connects to the cloud over API and generates a comprehensive graph/image of the environment. From there, the product can remotely check for misconfigurations, over-privileged IAM roles, opportunities for lateral movement, and more. This high-level view has made CSPM an excellent start for enterprises that simply want to understand what they have. While CSPMs are easy to deploy and quick to add value, the tradeoff is that there is only so much telemetry they can gather over API. These products will typically perform a scan of the environment every 12-24 hours, so organizations looking for more granular or real-time data will typically need additional tooling. There is a lot of innovation happening here with cloud APIs, so these gaps may become less pronounced over time.
- Cloud Workload Protection Platform (CWPP): These products are more granular than CSPM. They will typically deploy an agent on a host and flag lower-level misconfigurations that would not be captured by an agent-less product: e.g. if a container is over-privileged on a host, or if process execution deviates from standard baseline behavior. With recent advancements around technologies like eBPF, these agents are becoming less resource-intensive and providing even more granular telemetry than before.
- Cloud Detection & Response (CDR): This category is a more recent development, and focuses on helping organizations detect, investigate, and respond to incidents after they have already occurred. CDR programs will typically ingest data from a variety of sources, including but not limited to cloud infrastructure logs (e.g. AWS CloudTrail), application layer logs, eBPF agents, and more. SOC analysts can write custom detections to be applied to the stream of log data, or the platform can automatically flag anomalous deviations. While IAC scanning, CSPM, and CWPP are more preventative in nature, CDR is more reactive in nature. This does not mean that one thing is better than another, as a comprehensive cloud security program will entail multiple layers of coverage – it’s good to try and prevent things, but buyers also want to be prepared in the event that an attacker slips through the cracks.
- Cloud-Native Application Protection Program (CNAPP): Depending on who you ask, you may get a different definition here. My personal definition is that CNAPP includes all of the components of a cloud infrastructure security program. Meaning, at a minimum, CNAPP = CSPM + CWPP + CDR. Some may argue it also includes adjacencies like IAC scanning, CIEM, and NHI. I have even seen folks bundle in application security, which is ambitious. I tend to think of cloud security and application security as two distinct domains, where the former has CNAPP as a high-level classification over the underlying tools, and the latter has ASPM.
- Cloud Infrastructure Entitlement Management (CIEM): CIEM is all about managing internal developer access to infrastructure. Given the tremendous data privacy implications of storing user data in cloud-hosted databases, managing internal developer access has become increasingly critical with time. While existing categories like IGA and PAM have mostly specialized in managing access to applications, cloud infrastructure remains a more complex, nuanced, and ephemeral surface area, thus requiring dedicated tooling.
- Non-Human Identity (NHI): NHI is a bleeding-edge trend that has prompted an explosion of companies in the last 12 months. This category is built on an understanding that cloud applications require many different technical components to work together, such as service accounts, storage accounts, access keys, key management systems, IAM roles pertaining to sensitive data stores, and more. Much like employees navigating a corporate office with a key card, these components require authorizations to sensitive parts of an application in order for the whole operation to run smoothly. While generating a central system of record for human identities is a well-solved problem through IDPs like Okta and Active Directory, the same has not been done for these non-human identities. New companies here take a variety of approaches, but are broadly focused on inventorying, authorizing, or monitoring these low-level technical components. Recent breaches that exemplify non-human identity risk include the 2023 breach of Microsoft’s AI team, wherein a misconfigured Azure SAS token resulted in 38TB of internal GitHub and Teams data leaking.
- Remediation Ops (RemOps): The maturity of CSPM adoption has had a further knock-on effect in terms of alert sprawl. Security teams are now wrangling with misconfigurations and alerts across yet another domain: endpoint, application, network, identity, email, and now, also cloud infrastructure. This tipping point has prompted the creation of a new category that aggregates, correlates, and prioritizes findings across these domains to make the alert sprawl more manageable. These products will sometimes also handle the burdensome task of identifying the right person to route each alert to.
While many of the above categories are nascent, and some are not conventionally in the cloud security wheelhouse, I would broadly classify them all as opportunities that exist because of the increased maturity of enterprise cloud programs. In other words, if a cloud security program starts with a CSPM, it may well lead to adoption of one or more of the above categories further down the road. In the long run, the prioritization and buying process may also look completely different than what we see today. We are in the early innings of a massive and entirely new domain for security, which lends to both exciting opportunities and interesting open questions.
Open questions
Best-of-breed tooling vs. platform solutions
Those following the security industry closely may have seen the recent news around Palo Alto Networks’s Q2-2024 earnings, in which the company made the bold decision of offering certain product lines for free in order to drive broader platform adoption. The bet here is that the industry is moving towards vendor consolidation, and that customers will prefer larger platform solutions over managing best-of-breed point products. History shows that the industry tends to oscillate between the two, and that preferences are a function of interest rates and the broader business climate. During contractionary periods, security teams look for opportunities to cut spend and consolidate tools into a smaller list of trusted vendors.
Given Wiz’s ambition of graduating into a broader cloud security platform, one of the big open questions here is how emerging startups can compete against fast-moving incumbents with products in multiple categories. It could be that the market is big enough to support everyone all at once, but in competing with a soon-to-be platform like Wiz, founders will need to be thoughtful in crafting their initial product and landing motion.
CDR, XDR, and SIEMs: Competing for detection & response in a new domain
Cloud workloads have introduced yet another stream of real-time data for SOC analysts to wrestle with. An interesting dynamic that has emerged here is whether enterprises will leverage detection and response tools that are tailored for this specific domain (e.g. CDR), or whether they will simply feed the new cloud telemetry into existing SOC data lakes (e.g. SIEMs and XDR platforms), which have shared context from other domains as well.
On the XDR front, CrowdStrike recently announced that their cloud security product has crossed $400m in ARR, largely by just re-platforming their endpoint agent to also support cloud workloads. While this certainly speaks to the demand for real-time detection, investigation, and response for the cloud, I am curious how enterprises will balance more specialized tools like CDR alongside more generalist, existing investments like SIEMs and XDR.
IAM becomes more complicated
As my friend Rak pointed out in his excellent essay on identity, managing permissions is hard. Doing so for a new domain that is both faster-changing and more ephemeral than what existing IAM systems are designed for, is even harder. Microsoft recently published an eye-opening report on the State of Cloud Permission Risks, highlighting some of the blind spots that are now emerging for companies wrangling infrastructure permissions:
- On average, human identities only leverage only 1% of their granted permissions to cloud infrastructure. In other words, most folks are over-privileged by a factor of 99x.
- Cloud workload identities tend to use <5% of their granted permissions. The remaining 95% of permissions can potentially be hijacked for malicious behaviors.
- 80% of cloud workloads are considered to be inactive, making them prime targets for adversaries looking for unattended compute resources.
- There are an average of 200 services on offer from each CSP. Each of these services requires a unique set of permissions, which magnifies complexity tremendously.
As enterprises crack down on this problem space, it will be interesting to see the breadth of the platforms that emerge. Can a single vendor manage (1) human identity access to SaaS applications (IGA/PAM); (2) human identity access to cloud infrastructure (CIEM); and also (3) non-human identity access within the cloud (NHI)? Or are these problem spaces so distinct that each will support an independent outcome?
Closing thoughts
There is an element of humor in talking about “the shift to the cloud” as a novel thing in 2024, when most attention is on AI. This is a trend that has been over a decade in the making, but perhaps for that reason, the tremendous opportunities here have been hiding almost in plain sight. While cloud infrastructure adoption is finally crossing the chasm, there is still plenty of room for enterprises to scale their environments and graduate into more sophisticated tooling. As we continue to move along the maturity curve, more threat vectors emerge, and more security measures become needed.
We’ve seen existing domains like endpoint, network, and identity mature into massive markets that support multiple public companies and tens of billions of dollars in enterprise value. With cloud security, we’re witnessing the creation of an entirely new domain. Hyper-growth startups like Wiz and incumbents like CrowdStrike have done an incredible job capitalizing on this in recent years, but I believe that the space is immeasurably large, and that there’s certainly room for more. If you’re a founder, investor, or researcher spending time here, I’d love to chat. Feel free to drop me a note at shayan@scalevp.com.