As a security professional, I can attest that the lifeblood of any company is the sensitive data they process. To be useful this data needs to be connected to other applications, mashed-up with other data sources, and presented to a wide variety of mobile users, business owners and API endpoints. Protecting this data is the charter of a company’s Information Security team and the responsibility of all employees who work there. It is this dichotomy of access with restrictions that makes data security so hard to get right, creating risk and opportunity for every company. It’s no wonder that the cybersecurity startup market saw its highest level of funding in 2015: to $3.8 billion, a 238% growth in 5 years.
Last year I worked as an EIR with Scale Venture Partners spending a great deal of time meeting with CISOs to discuss what issues were most pressing to their programs and success. Following on that work, Scale partnered with the Ponemon Institute and Informatica to uncover what data security concerns were top-of-mind for security practitioners and how they approached the challenge. Ponemon surveyed 432 IT security practitioners who are responsible for IT security or data protection services within their company. This is the 2rd year of our survey, with some familiar themes and a few surprises. And because data security was a strong concern in last year’s study, we dove deeper to look at some of the underlying motivations.
What remained the same for security practitioners provides great opportunities for innovators and solution providers. Those who are “fighting the good fight” face a lot of headwind with growing risks of data breach, an expanding attack surface, and inability to measure whether their efforts are paying off or not.
Key Findings – What is still keeping us up at night?
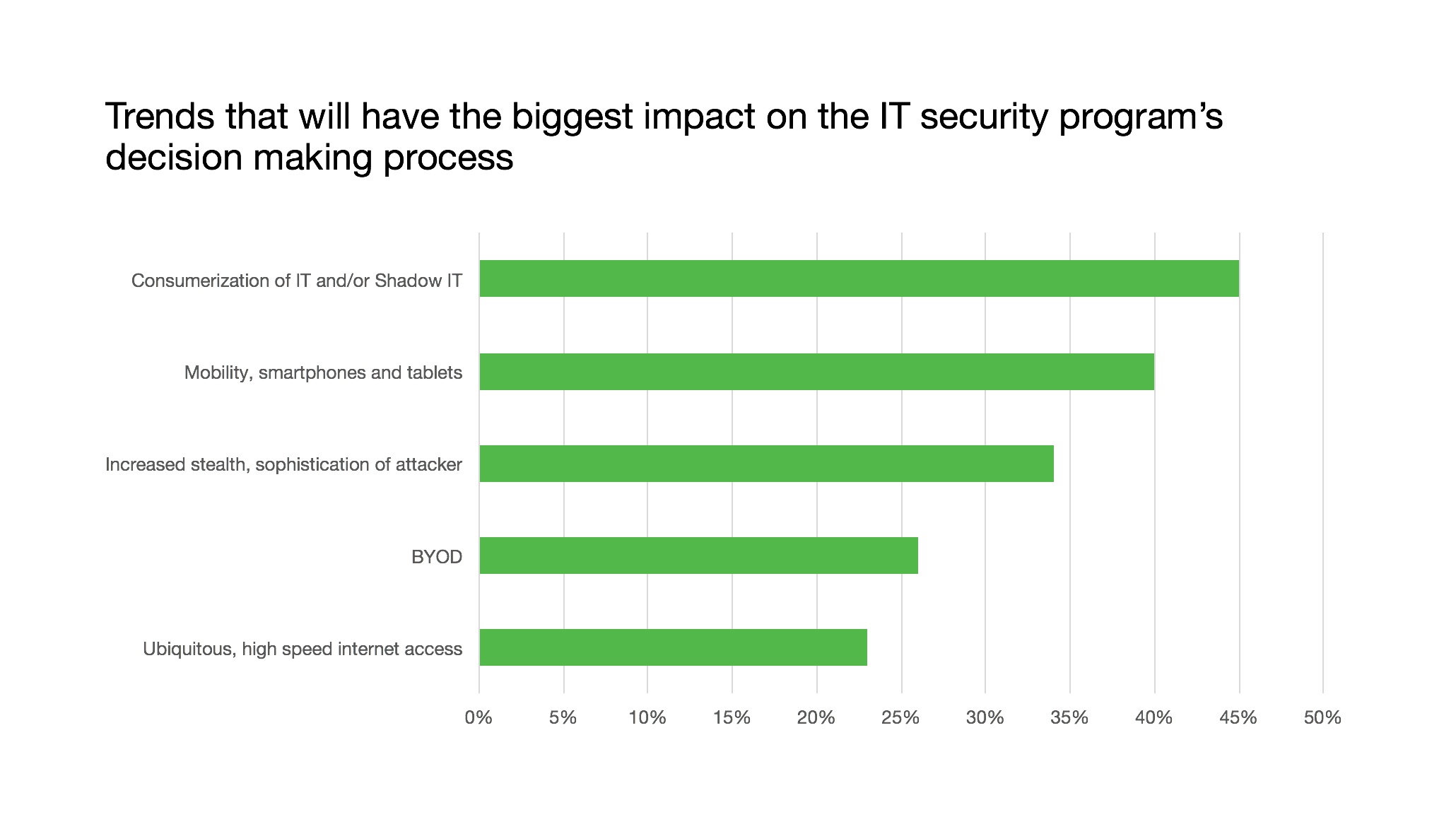
- Top forcing functions to security investments remain the consumerization of IT (aka “Shadow IT”), including cloud computing, and the growth of BYOD including smartphones and tablets. These technologies expand the locations where sensitive data resides, making it harder to protect while also making it easier for the business to consume and use. This trend shows no sign of slowing down, giving innovators plenty of runway to search for new solutions and giving practitioners choices in how they can protect information appropriate for their context.
- Despite all of their investments and activities, security teams cannot measure and report their business impact. Only 34% of survey respondents have metrics that report business value or meaningful results, which are ultimately what security teams need to secure budget and have business-level conversations beyond technology and the “attack-of-the-day”. Translating security and risk domain expertise into practical business terms remains a challenge.
- Data breaches are still a top concern, and are on the rise. This is amplified by a lack of confidence that they know where their sensitive data is in their company (almost two-thirds didn’t know), or can quantify the risk to sensitive data in databases, unstructured files or big data clusters.
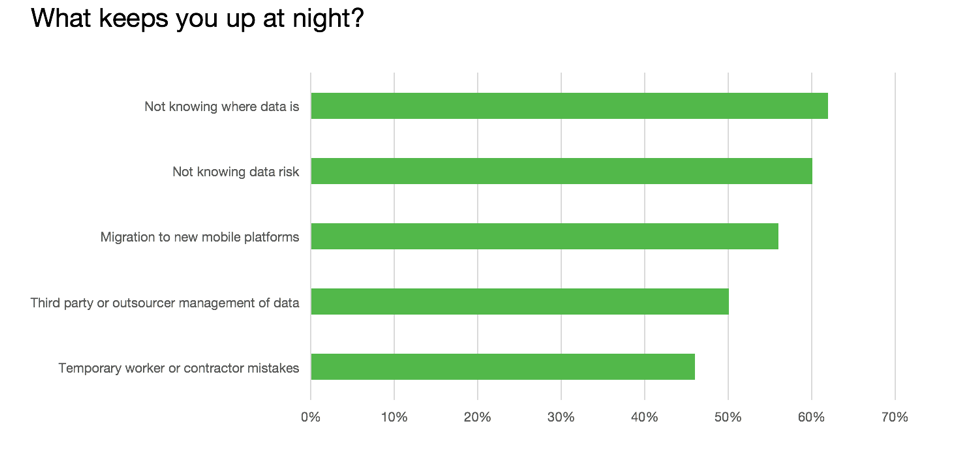
Thankfully, there is strong market fit for solutions that protect data moving to the cloud, both in terms of protection and visibility. New technologies show promise but are early in their adoption curve, while technologies designed to address malware are starting to show signs of maturation.
Key Findings – What was new or different for 2015?
- Secure Cloud Gateways are hot, with room to grow. In 2014 our survey respondents said cloud computing was a top-risk but very few noted it as an investment area. Around the same time, Gartner declared cloud security access brokers (CASB) the #1 spot in their top-10 list of Information Security technologies. Fast forward a year and 40% of respondents declared CASBs as a top security control for the next 3-5 years. This is consistent with the growth in cloud data and mobility and associated risks.
- Behavior-based monitoring technologies are still early. Despite a lot of hype over the past couple of years, user activity monitoring of sensitive data should be the sweet spot for this technology. While only one-quarter of respondents were applying this control to monitor their sensitive data systems, over half (54%) agreed that it should be used to track privileged user access.
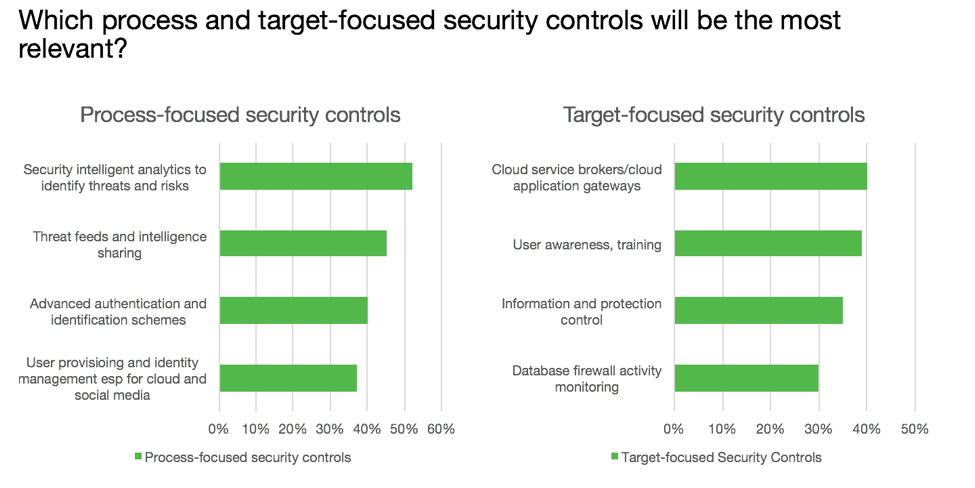
- Compliance and APT no longer security investment drivers. The cat-and-mouse game of APT and malware is well-understood: over half were confident in their anti-malware controls and only 11% declared this as a top risk to their organization. This could be a sign that this market segment is maturing. Compliance is also table-stakes for companies, with over one-half feeling confident in their current controls to manage their compliance requirements and only 5% noting it as a top risk.
- Managing data breach risk will drive investments across many areas. Lack of visibility, infrequent assessments or inability to assess the risk, and weak management support for sensitive data risk management are a dangerous combination. Survey respondents had little confidence in where their sensitive data was or how to quantify its risk. The numbers are sobering: on average, over 1/3 of our respondents’ data was considered sensitive, with respondents managing 4,000+ structured databases and 1,000+ big data nodes. More than half (54%) have no set schedule to do risk assessments of their sensitive data and few do it annually (less than 1-out-of-5). And even more concerning is that less than half believe that protecting sensitive data is important to their company. “Tone from the top” is a necessary condition to make security investments most effective, something that more Boards will likely drive in 2016 and beyond.
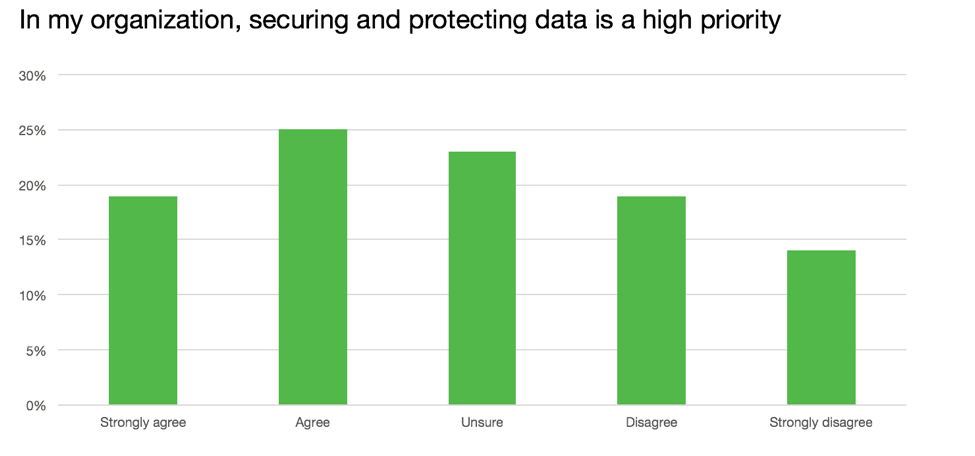
For companies that process sensitive data, it’s still a question of if-not-when the information will be lost or stolen. The first steps to keeping that information safe are knowing where it is, what threats it is vulnerable to, and what controls you have in place to keep it secure. The arms race that describes the technical security controls environment we live in today is not likely to let up anytime soon – we see continued strong innovation from startups who find novel ways to keep practitioners in the game and their data safe.
Collectively, the focus around detecting, preventing, and responding to data breaches is the paramount focus for companies and their security teams. This is a wide, broad technical challenge that also spans process and personnel issues. Protecting the confidentiality of data is a top investment area for security professionals for the next several years. And as the Internet of Things matures, protecting the integrity of these data flows will likely become a new area of concern. Perhaps an area to look into for next year’s survey…stay tuned!